How to check, if your NetScaler is affected by CVE-2019-19781: Citrix Exploit 1 and 2
You can check if your NetScaler is affected by CVE-2019-19781 with following commands:
Indicators of compromise
Template files
Apache Log files
Cron jobs
Backdoor scripts
Crypto miners
Firewall
Firmware updates
Indicators of compromise
To get an idea wether your Citrix
ADC is compromised I’d recommend to perform (at least!) the following steps
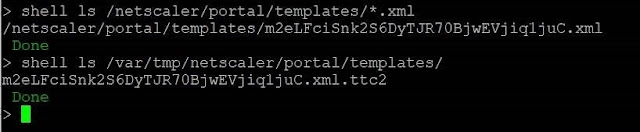
Template files
The exploits all write files to
two different directories. Scan those via:
shell ls /netscaler/portal/templates/*.xmlshell ls /var/tmp/netscaler/portal/templatesshell ls /var/vpn/bookmark/*.xml
If you find files similar to the
following you are likely to be compromised
Apache Log files
In addition, attempts to exploit
the system leave traces in the Apache httpaccess log files. Those you can
validate via:
shell cat /var/log/httpaccess.log | grep vpns | grep xmlshell cat /var/log/httpaccess.log | grep "/\.\./"shell gzcat /var/log/httpaccess.log.*.gz | grep vpns | grep xmlshell gzcat /var/log/httpaccess.log.*.gz | grep "/\.\./"
The following output is found on
a system that was exploited:
However, a guarantee can never
been given as attackers also might clean up their traces of the initial
exploitation. A few more things to validate are…
Cron jobs
Attackers have been observed to
obtain persistent access via scheduled tasks (“cron jobs” in Linux/BSD) to
maintain their access even if the vulnerability gets patched. Check your
crontab file for anomalies:
shell cat /etc/crontabshell crontab -l -u nobody
The following is the output of a
non-compromised system for you to compare:
Backdoor scripts
Running backdoors or other
malicious tasks are often executed as Perl or Python scripts. Check for the
presence of active running Perl or Python tasks:
shell ps -aux | grep pythonshell ps -aux | grep perl
If you see more then the “grep”
commands itself check the running scripts.
But beware, several Citrix ADC
system-native tasks might appear as well. Some run scheduled so run the query
again a few seconds later. Some are permanent (custom monitoring scripts for
Storefront for example). Check those scripts to make sure they weren’t altered.
Crypto miners
Several attacks have been observed
to install crypto miners. You can identifiy those by looking at the CPU intense
processes by running:
shell top -n 10
Should you see any other
processes but NSPPE-xx displaying high CPU usage you might have found a crypto
miner:
Firewall
In addition to Citrix ADC local
indicators observe your surrounding firewalls for any irregular traffic. Most
likely attackers will use the Citrix ADC as a jump host to penetrate the
network further.
Firmware updates
Citrix currently has no patch
available – however, according to a recent blog post Citrix announced release
dates for a permanent fix throughout January.
The announced release dates are:
27.1.2020
|
|
12.1
|
27.1.2020
|
12.0
|
20.1.2020
|
11.1
|
20.1.2020
|
10.5
|
31.1.2020
|
I recommend to schedule
an update ASAP after release and monitor the official advisory closely!







Comments
Post a Comment